Command IoT Devices Behind A Firewall: The Easy Way!
Ever wondered how to control your smart thermostat from across the globe? The ability to send commands to IoT devices nestled safely behind firewalls is no longer a futuristic fantasy, but a present-day reality that demands secure and ingenious solutions.
The challenge stems from the fundamental architecture of most IoT deployments. These devices, often lacking publicly reachable IP addresses, reside behind firewalls for security reasons. They can initiate communication with servers on the internet, thanks to the gateway router, but the reverse external entities initiating communication is typically blocked. This protective barrier prevents unauthorized access and shields IoT devices from potential threats, like prying eyes and malicious attacks. After all, the last thing anyone wants is a hacker turning off their home's security system or manipulating sensitive industrial controls.
However, the need to remotely manage and interact with these devices remains crucial. Think about monitoring environmental sensors in a remote agricultural field, controlling industrial machinery in a factory, or simply adjusting the lighting in your vacation home. These scenarios necessitate a secure and reliable method for sending commands to IoT devices lurking behind the firewall's defense.
| Topic | Description |
|---|---|
| IoT Device IP Addresses | Typically, IoT devices do not have publicly reachable IP addresses assigned for security reasons. |
| Firewall Functionality | Firewalls prevent direct access from the internet to devices behind them, enhancing security. |
| Outbound Communication | IoT devices can communicate with servers on the internet but not the other way around. |
| Security Motivation | This setup prevents unauthorized access and protects against hackers. |
| Remote Access Complexity | Accessing IoT devices behind a firewall is complex due to security measures. |
| Port Forwarding | Configuring the firewall to forward specific ports to the device's IP address. |
| Device Identification | Finding the device ID from a platform like SocketXP. |
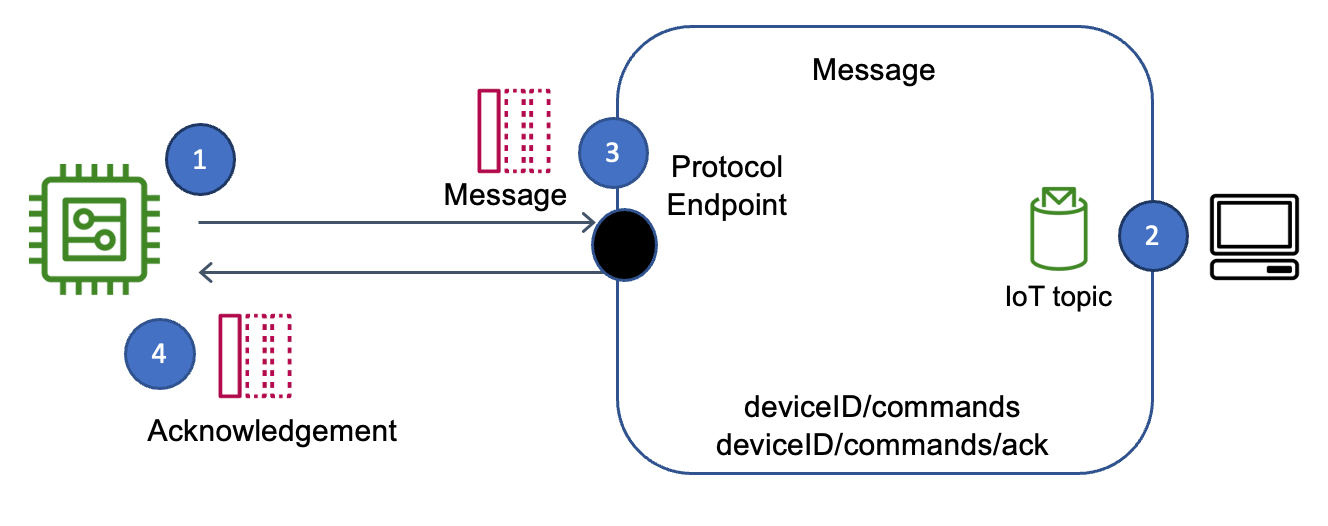
| Subscription Model | IoT devices subscribe to topics to listen for commands or actions. |
| Example Topic | An IoT device subscribing to the topic "office/floor1/bulb1". |
| Device Certificates | Device certificates are installed on firewalls to authenticate to logging services and IoT security. |
| Decryption Policies | Avoid using decryption policy rules on firewalls with device certificates. |
| Raspberry Pi Access | Methods to remotely access a Raspberry Pi behind a firewall or NAT router. |
| Direct Connection | Direct connection to a Raspberry Pi from anywhere as if on the local network. |
| Web Portal Control | Sending commands and batch jobs to a Raspberry Pi from a web portal. |
| No IP Discovery | No need to discover the device IP or change firewall settings. |
| IoT Firewall | IoT firewalls restrict access to prevent scans and reduce discovery chances by attackers. |
So, how do we bridge this gap? Several methods have emerged, each with its own set of trade-offs between security, complexity, and cost. One common approach involves configuring the firewall to forward specific ports to the IoT device's IP address. This essentially creates a tunnel through the firewall, allowing external traffic to reach the device. However, this method requires careful configuration and can potentially expose the device to vulnerabilities if not implemented correctly. It's like leaving a window slightly ajar convenient, but also an invitation for unwanted guests if not properly secured.
Another approach leverages the power of cloud-based IoT platforms. These platforms act as intermediaries, allowing devices to connect outbound to the cloud, while external commands are routed through the platform to the device. This offers a more secure and scalable solution, but it introduces a dependency on the cloud provider and requires careful consideration of data privacy and security policies. Think of it as using a trusted courier service to deliver your message secure and reliable, but you're relying on their infrastructure and protocols.
Consider a scenario where you want to control a smart lightbulb in your office. The lightbulb, being an IoT device, likely resides behind a firewall. To send a command to turn it on, you might use a cloud-based IoT platform. The lightbulb would subscribe to a specific topic, such as "office/floor1/bulb1." When you send a command to this topic through the platform, the lightbulb receives the message and executes the command, turning on the light. This approach eliminates the need to directly access the lightbulb's IP address or modify firewall settings.
Alternatively, solutions like SocketXP provide a way to discover the device ID from their portal, simplifying the process of identifying and managing individual devices. This streamlines the configuration process and reduces the risk of errors. The device ID acts as a unique identifier, allowing you to target specific devices with commands and configurations.
Security considerations are paramount when dealing with IoT devices behind firewalls. Installing device certificates on the firewall can enhance authentication and security, but it's crucial to avoid using decryption policy rules on firewalls that have these certificates installed. This is because the firewall may be unable to decrypt encrypted traffic for inspection and policy enforcement, potentially creating security loopholes. It's like adding a strong lock to your door but leaving the key under the doormat seemingly secure, but ultimately ineffective.
For those working with Raspberry Pi devices, several methods exist for remote access behind firewalls or NAT routers. One approach involves creating a direct connection as if the Raspberry Pi were on the local network, eliminating the need to discover its IP address or modify firewall settings. Another option is to use a web portal to send commands and batch jobs to the Raspberry Pi, providing a convenient and centralized control interface.
Ultimately, the choice of method depends on the specific requirements of the application, the security policies in place, and the available resources. Whether it's port forwarding, cloud-based platforms, or specialized solutions like SocketXP, the key is to carefully evaluate the trade-offs and implement a solution that provides both secure and reliable remote access to IoT devices behind firewalls. This proactive approach minimizes the chances of unauthorized access and maintains the integrity of your network.
Another crucial aspect is the implementation of an IoT firewall. Standard firewalls are not always equipped to handle the specific vulnerabilities and traffic patterns associated with IoT devices. An IoT firewall can restrict access, prevent unauthorized scans, and reduce the chances of an attacker even discovering a device on the network. This proactive approach minimizes the attack surface and strengthens the overall security posture. Think of it as adding an extra layer of security to your home, such as an alarm system or security cameras, to deter potential intruders.
In conclusion, accessing IoT devices behind firewalls requires careful planning and execution. By understanding the challenges, exploring the available methods, and prioritizing security, you can create a robust and reliable system for remotely managing and interacting with your IoT deployments. This ensures that you can harness the power of IoT without compromising the security of your network and devices.


Detail Author:
- Name : Soledad Becker
- Username : kariane.daniel
- Email : bashirian.emmie@yahoo.com
- Birthdate : 1971-02-09
- Address : 675 Stephan Grove Port Alexandremouth, SD 85286-8159
- Phone : +1 (678) 570-9936
- Company : Stroman Ltd
- Job : Director Of Talent Acquisition
- Bio : Rerum aut totam maiores est. Saepe qui quaerat molestiae minima facilis sint ad debitis. Aspernatur animi cum deleniti pariatur cupiditate facilis. Sed enim molestiae illo et sunt.
Socials
tiktok:
- url : https://tiktok.com/@karsonwilliamson
- username : karsonwilliamson
- bio : Eius officia ullam aspernatur aliquam id nemo quibusdam.
- followers : 587
- following : 1291
facebook:
- url : https://facebook.com/karson4950
- username : karson4950
- bio : At expedita ipsa quam similique dolorum. Hic ut unde est est laboriosam est.
- followers : 1704
- following : 156
twitter:
- url : https://twitter.com/karson9006
- username : karson9006
- bio : Et modi suscipit atque quam culpa exercitationem est at. Recusandae amet eum hic similique ex.
- followers : 2091
- following : 1006
linkedin:
- url : https://linkedin.com/in/kwilliamson
- username : kwilliamson
- bio : Ut vel vel blanditiis eum omnis alias.
- followers : 4962
- following : 941
instagram:
- url : https://instagram.com/kwilliamson
- username : kwilliamson
- bio : Rerum eligendi tenetur repellat itaque reiciendis. Omnis sunt incidunt molestiae et autem.
- followers : 782
- following : 1980